CrowdSec WAF QuickStart for HAProxy (SPOA)
Objectives
Set up the AppSec Component to protect web applications running behind HAProxy using the HAProxy SPOA remediation component.
You will:
- Enable CrowdSec AppSec (WAF) in the Security Engine.
- Install and configure
crowdsec-haproxy-spoa-bouncerso HAProxy can forward HTTP requests to AppSec. - Validate everything by triggering a test detection.
Prerequisites
- If you're new to the AppSec Component or Web Application Firewalls, start with the Introduction.
- It's assumed that you have already installed:
- CrowdSec Security Engine: for installation, refer to the QuickStart guide.
- HAProxy: already running and proxying your application(s).
- HAProxy SPOA Remediation Component:
crowdsec-haproxy-spoa-bouncer.
AppSec Component Setup
Collection installation
Install the main AppSec rule collections:
sudo cscli collections install crowdsecurity/appsec-virtual-patching crowdsecurity/appsec-generic-rules
These collections provide virtual patching (CVE rules), generic WAF detections, and the default AppSec configuration.
Setup the acquisition
Create /etc/crowdsec/acquis.d/appsec.yaml (see the AppSec datasource for the full reference):
appsec_configs:
- crowdsecurity/appsec-default
labels:
type: appsec
listen_addr: 127.0.0.1:7422
source: appsec
Restart CrowdSec:
sudo systemctl restart crowdsec
Remediation Component Setup
Install and configure the HAProxy SPOA bouncer
Read here how to install the SPOA remediation component: HAProxy SPOA remediation component docs.
Once the bouncer is installed and able to talk to CrowdSec LAPI, you only need to enable AppSec forwarding.
Enable AppSec forwarding in the bouncer (YAML)
In /etc/crowdsec/bouncers/crowdsec-spoa-bouncer.yaml, configure the AppSec endpoint the bouncer should query for WAF evaluation:
# AppSec (WAF forwarding)
appsec_url: "http://127.0.0.1:7422"
appsec_timeout: "200ms"
hosts:
- host: "*"
appsec:
always_send: false
Restart the bouncer:
sudo systemctl restart crowdsec-spoa-bouncer
Testing the AppSec Component + Remediation Component
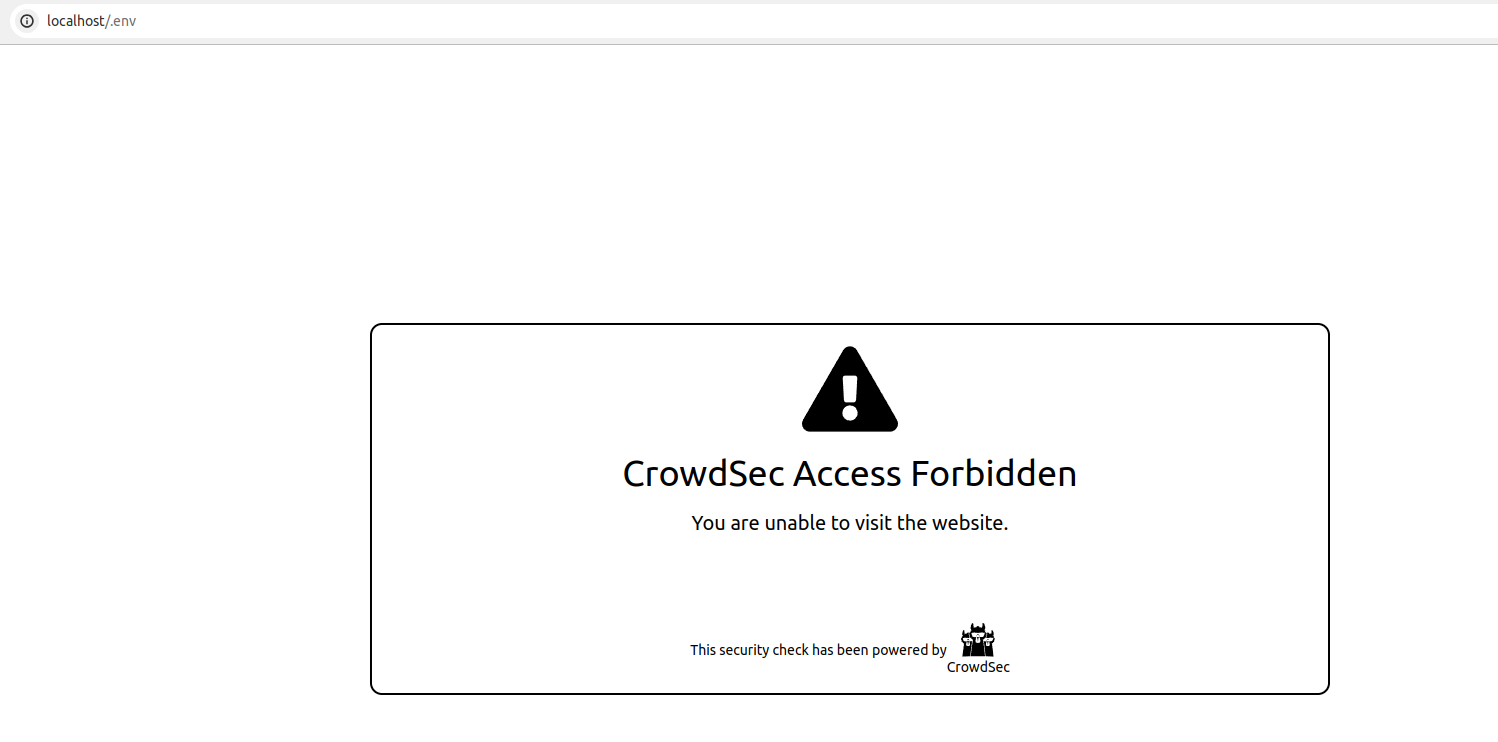
If you try to access http(s)://<your-haproxy-url>/.env, your request should be blocked:
curl -i http://<your-haproxy-url>/.env
You can also check AppSec metrics:
sudo cscli metrics show appsec
Explanation
What happened in the test above is:
- You requested
/.envthrough HAProxy. - HAProxy forwarded the request to the SPOA remediation component (SPOE/SPOA).
- The remediation component queried the AppSec Component at
appsec_url. - The request matched the AppSec rule to detect
.envaccess. - AppSec returned a blocking action (HTTP 403) to the remediation component.
- HAProxy blocked the request.
Next steps
- Monitor WAF alerts with
sudo cscli alerts listand in the CrowdSec Console. - Tune rules and configurations:
/appsec/configuration.mdand/appsec/configuration_rule_management.md. - Troubleshoot:
/appsec/troubleshooting.mdand HAProxy SPOA remediation component docs.

