CrowdSec WAF QuickStart for WordPress
Objectives
The goal of this quickstart is to set up the AppSec Component to safeguard web applications running on WordPress sites.
We'll deploy a set of rules designed to block well-known attacks and currently exploited vulnerabilities.
Additionally, we'll show how to monitor these alerts through the Console.
Prerequisites
-
If you're new to the AppSec Component or Web Application Firewalls, start with the Introduction for a better understanding.
-
It's assumed that you have already installed:
- CrowdSec Security Engine: for installation, refer to the QuickStart guide. The AppSec Component, which analyzes HTTP requests, is included within the security engine as a Acquisition.
- WordPress Remediation Component: installation instructions are available in the WordPress bouncer guide. The CrowdSec WordPress plugin enables you to protect your WordPress site against malicious traffic using CrowdSec's advanced threat detection and blocklist capabilities.
This component intercepts HTTP requests at the WordPress level and forwards them to the AppSec Component for analysis and action.
AppSec Component Setup
Collection installation
To begin setting up the AppSec Component, the initial step is to install a relevant set of rules.
We will utilize the crowdsecurity/appsec-virtual-patching collection, which offers a wide range of rules aimed at identifying and preventing the exploitation of known vulnerabilities.
This collection is regularly updated to include protection against newly discovered vulnerabilities. Upon installation, it receives automatic daily updates to ensure your protection is always current.
We also install the crowdsecurity/appsec-generic-rules collection. This collection contains detection scenarios for generic attack vectors. It provides protection in cases where specific scenarios for vulnerabilities do not exist yet.
On the machine where the Security Engine is installed, just execute the following command:
sudo cscli collections install crowdsecurity/appsec-virtual-patching crowdsecurity/appsec-generic-rules
Executing this command will install the following items:
- The AppSec Rules contain the definition of malicious requests to be matched and stopped
- The AppSec Configuration links together a set of rules to provide a coherent set
- The CrowdSec Parser and CrowdSec Scenario(s) bans for a longer duration repeating offenders
Setup the Acquisition
Having installed the required components, it's time to configure the CrowdSec acquisition datasource for the AppSec Component (AppSec datasource). This configuration allows WordPress to send requests to the AppSec Component for evaluation and decision-making.
Steps:
-
Create the acquisition directory (if it doesn't exist on your machine):
sudo mkdir -p /etc/crowdsec/acquis.d/ -
Create
/etc/crowdsec/acquis.d/appsec.yaml:/etc/crowdsec/acquis.d/appsec.yamlappsec_configs:
- crowdsecurity/appsec-default
labels:
type: appsec
listen_addr: 127.0.0.1:7422
source: appsec
The two important directives in this configuration file are:
appsec_configsis the list of AppSec Configurations that was included in the Collection we just installed.- the
listen_addris the IP and port the AppSec Component will listen to.
You can now restart CrowdSec:
sudo systemctl restart crowdsec
Testing the AppSec Component
Verify the AppSec Component is listening
To verify that the AppSec Component is running correctly, we can first check that the port 7422 is open and listening:
- Netstat
- SS
sudo netstat -tlpn | grep 7422
sudo ss -tlpn | grep 7422
Output example
tcp 0 0 127.0.0.1:7422 0.0.0.0:* LISTEN 12345/crowdsec
(Optional) Manually testing the AppSec Component with curl
Expand for short guide
Before we proceed with configuring the Remediation Component, let's verify that all our current setups are functioning correctly.
- Create a Remediation Component (Bouncer) API Key:
sudo cscli bouncers add test_waf -k this_is_a_bad_password
API key for 'test_waf':
this_is_a_bad_password
Please keep this key since you will not be able to retrieve it!
- Emit a legitimate request to the AppSec Component:
curl -X POST localhost:7422/ -i -H 'x-crowdsec-appsec-uri: /test' -H 'x-crowdsec-appsec-ip: 192.168.1.1' -H 'x-crowdsec-appsec-host: foobar.com' -H 'x-crowdsec-appsec-verb: POST' -H 'x-crowdsec-appsec-api-key: this_is_a_bad_password'
Which will give us an answer such as:
HTTP/1.1 200 OK
Date: Tue, 30 Jan 2024 15:43:50 GMT
Content-Length: 36
Content-Type: text/plain; charset=utf-8
{"action":"allow","http_status":200}
- Emit a malevolent request to the Appsec Component:
curl -X POST localhost:7422/ -i -H 'x-crowdsec-appsec-uri: /.env' -H 'x-crowdsec-appsec-ip: 192.168.1.1' -H 'x-crowdsec-appsec-host: foobar.com' -H 'x-crowdsec-appsec-verb: POST' -H 'x-crowdsec-appsec-api-key: this_is_a_bad_password'
Our request is detected and blocked by the AppSec Component:
HTTP/1.1 403 Forbidden
Date: Tue, 30 Jan 2024 15:57:08 GMT
Content-Length: 34
Content-Type: text/plain; charset=utf-8
{"action":"ban","http_status":403}
Let's now delete our test API Key:
sudo cscli bouncers delete test_waf
Remediation Component Setup
Since our AppSec Component is active and listening, we can now configure the WordPress Remediation Component to forward requests to it.
The WordPress bouncer includes built-in AppSec support that can be enabled through the plugin's admin interface.
Enable AppSec in WordPress Plugin
-
Log in to your WordPress admin panel
-
Navigate to the CrowdSec plugin settings (
CrowdSecin your admin menu) -
Go to the
Advancedsection -
Find the
AppSec componentconfiguration section -
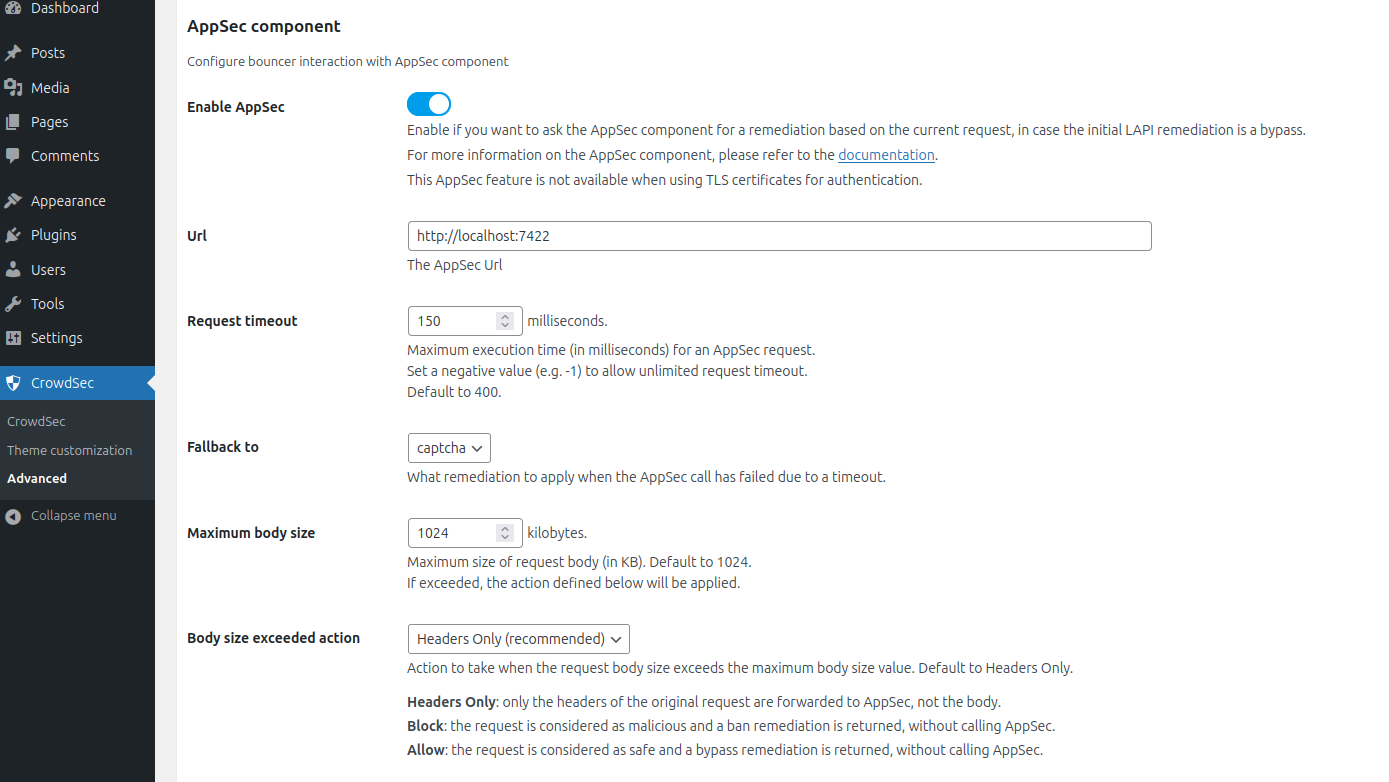
Enable AppSec and configure the connection:
- Enable AppSec: Check this box to enable AppSec functionality
- URL: Set to
http://127.0.0.1:7422(or your custom AppSec Component address) - Request timeout: Default is 400 milliseconds (adjust as needed)
- Fallback to: Choose
captcha(recommended) for when AppSec calls fail - Maximum body size: Default is 1024 KB
- Body size exceeded action: Choose
headers_only(recommended)
Testing the AppSec Component + Remediation Component
To test the AppSec functionality, you need to make a request that will go through the WordPress loading process. Try accessing a WordPress page with a malicious payload in the URL parameters or body. For example, we can post a request with a body that contains a malicious payload, such as a Remote Code Execution (CVE-2022-22965) attempt.
curl -X POST https://<your-wordpress-uri>/ -d "class.module.classLoader.resources." -o /dev/null -s -w "%{http_code}"
When the AppSec Component detects such a malicious request, you'll see that the response is a 403 (Forbidden) status code, indicating that the request was blocked.
If your test is not successful, please refer to the Health check and troubleshoot guide for help.
You can also look at the metrics from cscli metrics show appsec which will display:
- the number of requests processed by the AppSec Component
- Individual rule matches
Example Output
Appsec Metrics:
╭─────────────────┬───────────┬─────────╮
│ Appsec Engine │ Processed │ Blocked │
├─────────────────┼───────────┼─────────┤
│ 127.0.0.1:7422/ │ 2 │ 1 │
╰─────────────────┴───────────┴─────────╯
Appsec '127.0.0.1:7422/' Rules Metrics:
╭─────────────────────────────────────┬───────────╮
│ Rule ID │ Triggered │
├─────────────────────────────────────┼───────────┤
│ crowdsecurity/vpatch-CVE-2022-22965 │ 1 │
╰─────────────────────────────────────┴───────────╯
Explanation
What happened in the test that we just did is:
- We made a request with malicious payload to our WordPress site
- The WordPress bouncer plugin intercepted the request as part of the WordPress loading process
- The bouncer first checked with the local CrowdSec API for any existing decisions
- Since there was no existing ban decision, the bouncer forwarded the request to the AppSec Component at
http://127.0.0.1:7422 - Our AppSec Component analyzed the request and matched it against the appropriate AppSec rules (here
crowdsecurity/vpatch-CVE-2022-22965rule) - The AppSec Component returned an HTTP 403 response to the WordPress bouncer, indicating that the request must be blocked
- The WordPress bouncer then presented the visitor with the configured ban page
Integration with the Console
If you haven't yet, follow the guide about how to enroll your Security Engine in the Console.
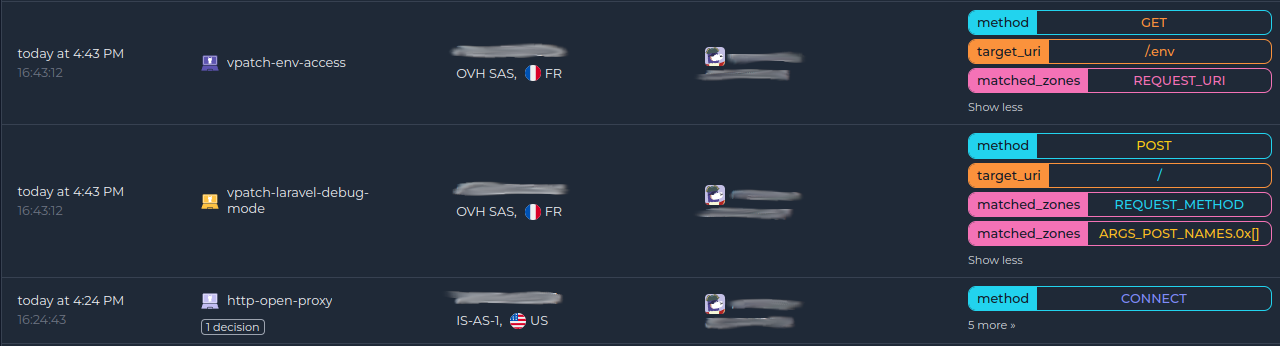
Once done, all your alerts, including the ones generated by the AppSec Component, appear in the Console:
WordPress-Specific Considerations
Understanding Plugin Limitations
The WordPress bouncer has some inherent limitations you should be aware of:
-
WordPress Loading Process: The plugin only protects requests that go through the WordPress core loading process. Direct access to PHP files outside of WordPress won't be protected.
-
Static Files: Requests for non-PHP files (like
.env,.sql, or other static files) won't be processed by the plugin since they don't go through PHP. -
Auto Prepend File Mode: For comprehensive protection, consider enabling auto prepend file mode in the plugin settings to ensure all PHP scripts are protected.
Next steps
You are now running the AppSec Component on your CrowdSec Security Engine.
As the next steps, you can:
- Look at WAF Deployment Strategies to discover how to gradually improve your WAF security.
- Look at the Rules syntax and creation process to create your own and contribute
- Take a look at the benchmarks

