Webhook
Install the webhook integration
Installing the webhook integration allows you to configure any webhook URL when configuring your notification rule.
- In the CrowdSec Console, navigate to Settings > Integrations and then select Activate in the Webhook row.
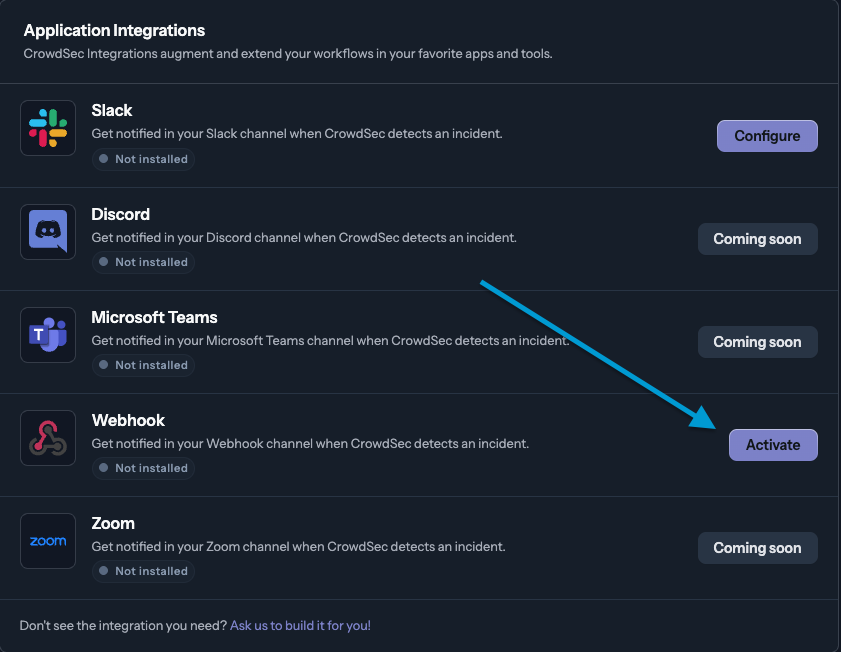
- You should be redirected to the Webhook integration page. You can now create a notification rule by navigating to the Rules tab.
Create a notification rule
-
In the CrowdSec Console, navigate to Settings > Integrations > Webhook go to the Rules tab and click on Add rule.
-
Follow the steps in the Create a notification rule documentation to create your rule.
Configure webhook
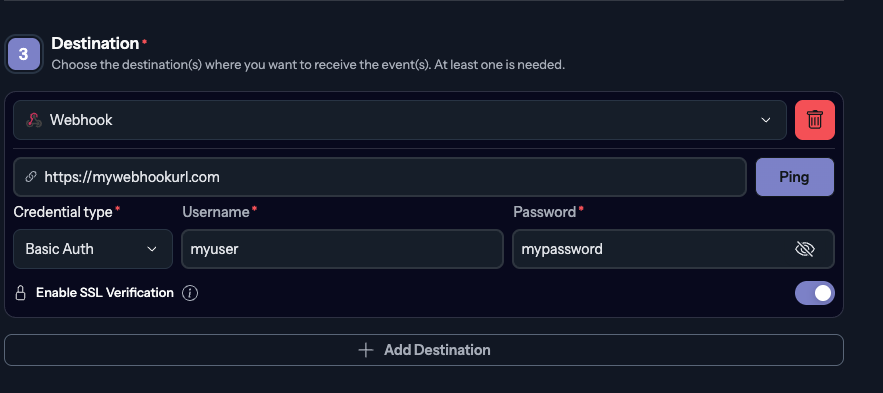
Authentication
For the authentication part, the webhook integration supports the following methods:
Bearer (HTTP Header)
You can provide a specific header name with a specific header value for the webhook integration to authenticate against your webhook URL.
Typically we would expect users to use Authorization header using the Bearer scheme.
However, you can send any header and any value.
Basic Authentication
You can use basic auth (user/password) for the webhook integration to authenticate against your webhook URL
Configuration
You can configure your custom Webhook URL and authentication by adding a new destination in your notification rule:
Retry
If a notification fails to be sent through the webhook integration, the system will automatically retry sending it. It will try up to 5 times, with a longer wait between each attempt.
Retry Scenarios
The webhook integration will retry in the following scenarios:
- Non-200 HTTP status codes returned from the webhook endpoint
- Network connectivity issues:
- DNS resolution failures
- Connection timeouts (30 seconds to receive a response)
- Connection refused errors
- TLS/SSL handshake failures (Disable SSL verification if self-signed or non-trusted root CA)
- Webhook endpoint is temporarily unavailable
Events Category
Threat Hunting
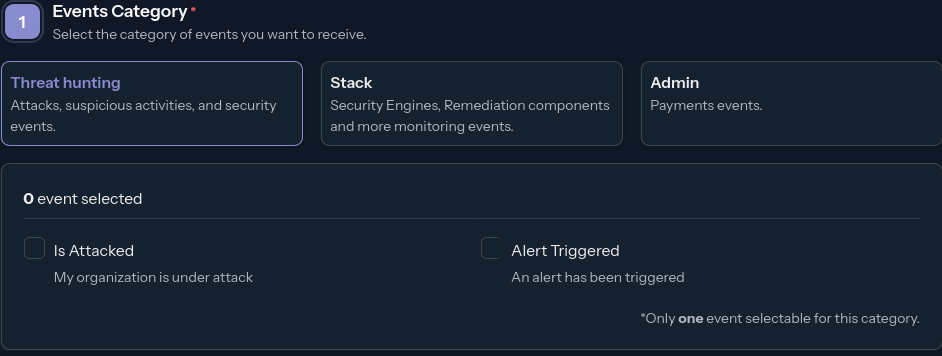
Is Attacked
Your organization is under attack, known as the am I under attack feature documentation
{
"metadata": {
"version": 1,
"issuer": "crowdsec.net"
},
"details": {
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2021-07-29T12:00:00+00:00",
"event_type": "am_i_under_attack",
"start_date": "2025-05-26T12:00:00Z",
"end_date": "2025-05-26T14:00:00Z",
"segments_with_anomaly": [
"2025-05-26T12:15:00Z",
"2025-05-26T12:45:00Z",
"2025-05-26T13:30:00Z"
],
"total_signals": 42,
"report_data": {
"is_attack_detected": true,
"unique_detections": 5,
"total_detections": 23,
"attack_length": 7200,
"first_detection_date": "2025-05-26T12:10:00Z",
"last_detection_date": "2025-05-26T13:55:00Z",
"increased_percentage": 67.5
},
"watchers": [
{
"watcher_uuid": "abc123-watcher-uuid-001",
"total_signals": 20
},
{
"watcher_uuid": "def456-watcher-uuid-002",
"total_signals": 22
}
]
}
}
JSON Schema
{
"$defs": {
"AIUAAnomalyReport": {
"description": "Key stats about the anomaly detection results.",
"properties": {
"is_attack_detected": {
"description": "An attack has been detected",
"title": "Is Attack Detected",
"type": "boolean"
},
"unique_detections": {
"description": "The number of unique detections",
"title": "Unique Detections",
"type": "integer"
},
"total_detections": {
"description": "The total number of detections",
"title": "Total Detections",
"type": "integer"
},
"attack_length": {
"description": "The length of the attack",
"title": "Attack Length",
"type": "integer"
},
"first_detection_date": {
"description": "The first detection date",
"format": "date-time",
"title": "First Detection Date",
"type": "string"
},
"last_detection_date": {
"description": "The last detection date",
"format": "date-time",
"title": "Last Detection Date",
"type": "string"
},
"increased_percentage": {
"description": "The increased percentage",
"title": "Increased Percentage",
"type": "number"
}
},
"required": [
"is_attack_detected",
"unique_detections",
"total_detections",
"attack_length",
"first_detection_date",
"last_detection_date",
"increased_percentage"
],
"title": "AIUAAnomalyReport",
"type": "object"
},
"AIUAWatcherReport": {
"description": "Key stats about the anomaly detection results.",
"properties": {
"watcher_uuid": {
"description": "The watcher UUID",
"title": "Watcher Uuid",
"type": "string"
},
"total_signals": {
"description": "The total number of signals",
"title": "Total Signals",
"type": "integer"
}
},
"required": [
"watcher_uuid",
"total_signals"
],
"title": "AIUAWatcherReport",
"type": "object"
}
},
"type": "object",
"properties": {
"metadata": {
"type": "object",
"properties": {
"version": {
"type": "integer",
"const": 1
},
"issuer": {
"type": "string",
"const": "crowdsec.net"
}
},
"required": [
"version",
"issuer"
]
},
"details": {
"properties": {
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"event_type": {
"const": "am_i_under_attack",
"default": "am_i_under_attack",
"title": "Event Type",
"type": "string"
},
"start_date": {
"description": "The attack start date",
"format": "date-time",
"title": "Start Date",
"type": "string"
},
"end_date": {
"description": "The attack end date",
"format": "date-time",
"title": "End Date",
"type": "string"
},
"segments_with_anomaly": {
"default": [],
"description": "List of detection timestamps",
"items": {
"format": "date-time",
"type": "string"
},
"title": "Segments With Anomaly",
"type": "array"
},
"total_signals": {
"default": 0,
"description": "The total number of signals",
"title": "Total Signals",
"type": "integer"
},
"report_data": {
"anyOf": [
{
"$ref": "#/$defs/AIUAAnomalyReport"
},
{
"type": "null"
}
],
"default": null,
"description": "Anomaly report data"
},
"watchers": {
"default": [],
"description": "Watcher reports",
"items": {
"$ref": "#/$defs/AIUAWatcherReport"
},
"title": "Watchers",
"type": "array"
}
},
"required": [
"event_id",
"organization_id",
"event_timestamp",
"event_type",
"start_date",
"end_date",
"segments_with_anomaly",
"total_signals",
"report_data",
"watchers"
],
"title": "AmIUnderAttack",
"type": "object"
}
},
"required": [
"metadata",
"details"
]
}
Alert Triggered
Your enrolled engines have detected malicious activity and the payload of the webhook contains information surrounding the alert.
{
"metadata": {
"version": 1,
"issuer": "crowdsec.net"
},
"details": {
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2021-07-29T12:00:00+00:00",
"event_type": "alert_triggered",
"uuid": "alert-uuid-1234",
"message": "Suspicious SSH behavior detected",
"scenario": "ssh-brute-force",
"behaviors": [
{
"name": "Brute Force",
"description": "Multiple failed SSH login attempts detected in short time",
"label": "SSH Brute Force"
},
{
"name": "Port Scan",
"description": "Scanning activity detected on multiple ports",
"label": "Scan"
}
],
"start_at": "2025-05-26T18:00:00Z",
"stop_at": "2025-05-26T18:10:00Z",
"target": {
"ip": "192.168.1.10",
"id": "machine-01",
"name": "internal-server-01"
},
"source": {
"scope": "ip",
"value": "203.0.113.25",
"as_name": "ExampleISP",
"as_number": 64512,
"country": "US",
"city": "San Francisco",
"latitude": 37.7749,
"longitude": -122.4194,
"rdns": "25.113.0.203.example.com"
},
"is_manual_decision": false,
"scenario_confidence": 85
}
}
JSON Schema
{
"$defs": {
"AlertBehavior": {
"properties": {
"name": {
"description": "The attack behavior name",
"title": "Name",
"type": "string"
},
"description": {
"description": "The attack behavior description",
"title": "Description",
"type": "string"
},
"label": {
"description": "The attack behavior label",
"title": "Label",
"type": "string"
}
},
"required": [
"name",
"description",
"label"
],
"title": "AlertBehavior",
"type": "object"
},
"AlertTarget": {
"properties": {
"ip": {
"description": "The IP targeted by the attack",
"title": "Ip",
"type": "string"
},
"id": {
"description": "The id of the machine targeted by the attack",
"title": "Id",
"type": "string"
},
"name": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "The name of the machine targeted by the attack",
"title": "Name"
}
},
"required": [
"ip",
"id"
],
"title": "AlertTarget",
"type": "object"
},
"AlertSource": {
"properties": {
"scope": {
"description": "The scope of the value",
"title": "Scope",
"type": "string"
},
"value": {
"description": "The value of the source",
"title": "Value",
"type": "string"
},
"as_name": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "The AS name of the source",
"title": "As Name"
},
"as_number": {
"anyOf": [
{
"type": "integer"
},
{
"type": "null"
}
],
"default": null,
"description": "The AS number of the source",
"title": "As Number"
},
"country": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "The country of the source",
"title": "Country"
},
"city": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "The city of the source",
"title": "City"
},
"latitude": {
"anyOf": [
{
"type": "number"
},
{
"type": "null"
}
],
"default": null,
"description": "The latitude of the source",
"title": "Latitude"
},
"longitude": {
"anyOf": [
{
"type": "number"
},
{
"type": "null"
}
],
"default": null,
"description": "The longitude of the source",
"title": "Longitude"
},
"rdns": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "The rDNS of the source",
"title": "Rdns"
}
},
"required": [
"scope",
"value"
],
"title": "AlertSource",
"type": "object"
}
},
"type": "object",
"properties": {
"metadata": {
"type": "object",
"properties": {
"version": {
"type": "integer",
"const": 1
},
"issuer": {
"type": "string",
"const": "crowdsec.net"
}
},
"required": [
"version",
"issuer"
]
},
"details": {
"properties": {
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"event_type": {
"const": "alert_triggered",
"default": "alert_triggered",
"title": "Event Type",
"type": "string"
},
"uuid": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "The alert UUID",
"title": "Uuid"
},
"message": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "The alert message",
"title": "Message"
},
"scenario": {
"description": "The attack scenario",
"title": "Scenario",
"type": "string"
},
"behaviors": {
"default": [],
"description": "The attack behaviors",
"items": {
"$ref": "#/$defs/AlertBehavior"
},
"title": "Behaviors",
"type": "array"
},
"start_at": {
"description": "The attack start time",
"format": "date-time",
"title": "Start At",
"type": "string"
},
"stop_at": {
"description": "The attack stop time",
"format": "date-time",
"title": "Stop At",
"type": "string"
},
"target": {
"$ref": "#/$defs/AlertTarget",
"description": "The target of the attack"
},
"source": {
"$ref": "#/$defs/AlertSource",
"description": "The source of the attack"
},
"is_manual_decision": {
"default": false,
"description": "Whether the decision was created manually",
"title": "Is Manual Decision",
"type": "boolean"
},
"scenario_confidence": {
"default": 0,
"description": "The confidence of the scenario",
"title": "Scenario Confidence",
"type": "integer"
}
},
"required": [
"event_id",
"organization_id",
"event_timestamp",
"event_type",
"uuid",
"message",
"scenario",
"behaviors",
"start_at",
"stop_at",
"target",
"source",
"is_manual_decision",
"scenario_confidence"
],
"title": "AlertTriggered",
"type": "object"
}
},
"required": [
"metadata",
"details"
]
}
Stack
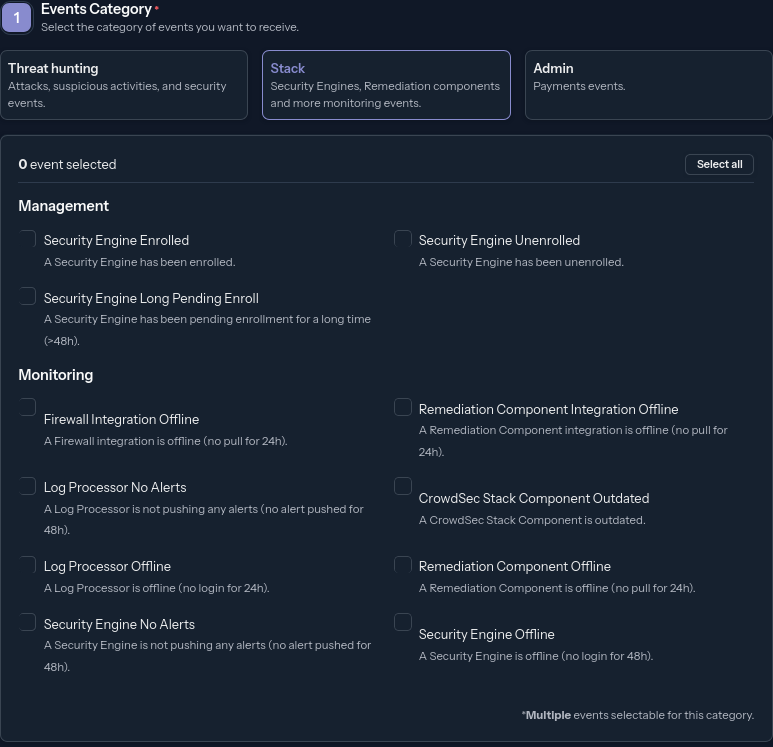
Security Engine Enrolled
A engine has been accepted to be enrolled within your organization or personal account
{
"metadata": {
"version": 1,
"issuer": "crowdsec.net"
},
"details": {
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2021-07-29T12:00:00+00:00",
"id": "12345677732339c3d12345164a8426sbnk6ll4iaazda1234",
"version": "v1.6.3-rc4",
"os" : {"name" : "ubuntu", "version": "22.04"},
"event_type": "security_engine_enrolled"
}
}
JSON Schema
{
"$defs": {
"OperatingSystem": {
"properties": {
"name": {
"title": "Name",
"type": "string"
},
"version": {
"title": "Version",
"type": "string"
}
},
"required": [
"name",
"version"
],
"title": "OperatingSystem",
"type": "object"
}
},
"type": "object",
"properties": {
"metadata": {
"type": "object",
"properties": {
"version": {
"type": "integer",
"const": 1
},
"issuer": {
"type": "string",
"const": "crowdsec.net"
}
},
"required": [
"version",
"issuer"
]
},
"details": {
"properties": {
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"id": {
"description": "ID of the security engine",
"examples": [
"12345677732339c3d12345164a8426sbnk6ll4iaazda1234"
],
"title": "Id",
"type": "string"
},
"version": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "Version of the security engine",
"examples": [
"v1.6.3-rc4"
],
"title": "Version"
},
"os": {
"anyOf": [
{
"$ref": "#/$defs/OperatingSystem"
},
{
"type": "null"
}
],
"default": null,
"description": "Operating System of the security engine",
"examples": [
"Linux"
]
},
"event_type": {
"const": "security_engine_enrolled",
"default": "security_engine_enrolled",
"title": "Event Type",
"type": "string"
}
},
"required": [
"event_id",
"organization_id",
"event_timestamp",
"id",
"version",
"os",
"event_type"
],
"title": "SecurityEngineEnrolled",
"type": "object"
}
},
"required": [
"metadata",
"details"
]
}
Security Engine Unenrolled
Security engine has been removed from your organization or personal account
This can happen under these scenarios:
- User has manually removed the engine
- Automatic removal has occurred due to
Settings > Security Engines > Inactive Policy
{
"metadata": {
"version": 1,
"issuer": "crowdsec.net"
},
"details": {
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2021-07-29T12:00:00+00:00",
"id": "12345677732339c3d12345164a8426sbnk6ll4iaazda1234",
"version": "v1.6.3-rc4",
"os" : {"name" : "ubuntu", "version": "22.04"},
"event_type": "security_engine_unenrolled"
}
}
JSON Schema
{
"$defs": {
"OperatingSystem": {
"properties": {
"name": {
"title": "Name",
"type": "string"
},
"version": {
"title": "Version",
"type": "string"
}
},
"required": [
"name",
"version"
],
"title": "OperatingSystem",
"type": "object"
}
},
"type": "object",
"properties": {
"metadata": {
"type": "object",
"properties": {
"version": {
"type": "integer",
"const": 1
},
"issuer": {
"type": "string",
"const": "crowdsec.net"
}
},
"required": [
"version",
"issuer"
]
},
"details": {
"properties": {
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"id": {
"description": "ID of the security engine",
"examples": [
"12345677732339c3d12345164a8426sbnk6ll4iaazda1234"
],
"title": "Id",
"type": "string"
},
"version": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "Version of the security engine",
"examples": [
"v1.6.3-rc4"
],
"title": "Version"
},
"os": {
"anyOf": [
{
"$ref": "#/$defs/OperatingSystem"
},
{
"type": "null"
}
],
"default": null,
"description": "Operating System of the security engine",
"examples": [
"Linux"
]
},
"event_type": {
"const": "security_engine_unenrolled",
"default": "security_engine_unenrolled",
"title": "Event Type",
"type": "string"
}
},
"required": [
"event_id",
"organization_id",
"event_timestamp",
"id",
"version",
"os",
"event_type"
],
"title": "SecurityEngineUnenrolled",
"type": "object"
}
},
"required": [
"metadata",
"details"
]
}
Security Engine Long Pending Enroll
{
"metadata": {
"version": 1,
"issuer": "crowdsec.net"
},
"details": {
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2021-07-29T12:00:00+00:00",
"id": "12345677732339c3d12345164a8426sbnk6ll4iaazda1234",
"version": "v1.6.3-rc4",
"os" : {"name" : "ubuntu", "version": "22.04"},
"event_type": "security_engine_long_pending_enroll"
}
}
JSON Schema
{
"$defs": {
"OperatingSystem": {
"properties": {
"name": {
"title": "Name",
"type": "string"
},
"version": {
"title": "Version",
"type": "string"
}
},
"required": [
"name",
"version"
],
"title": "OperatingSystem",
"type": "object"
}
},
"type": "object",
"properties": {
"metadata": {
"type": "object",
"properties": {
"version": {
"type": "integer",
"const": 1
},
"issuer": {
"type": "string",
"const": "crowdsec.net"
}
},
"required": [
"version",
"issuer"
]
},
"details": {
"properties": {
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"id": {
"description": "ID of the security engine",
"examples": [
"12345677732339c3d12345164a8426sbnk6ll4iaazda1234"
],
"title": "Id",
"type": "string"
},
"version": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "Version of the security engine",
"examples": [
"v1.6.3-rc4"
],
"title": "Version"
},
"os": {
"anyOf": [
{
"$ref": "#/$defs/OperatingSystem"
},
{
"type": "null"
}
],
"default": null,
"description": "Operating System of the security engine",
"examples": [
"Linux"
]
},
"event_type": {
"const": "security_engine_long_pending_enroll",
"default": "security_engine_long_pending_enroll",
"title": "Event Type",
"type": "string"
}
},
"required": [
"event_id",
"organization_id",
"event_timestamp",
"id",
"version",
"os",
"event_type"
],
"title": "LongPendingEnroll",
"type": "object"
}
},
"required": [
"metadata",
"details"
]
}
Firewall Integration Offline
A Firewall Integration has been classified as offline.
This can happen for these scenarios:
- Firewall has not actively pulled the contents for over 24 hours.
{
"metadata": {
"version": 1,
"issuer": "crowdsec.net"
},
"details": {
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2021-07-29T12:00:00+00:00",
"id": "12345677732339c3d12345164a8426sbnk6ll4iaazda1234",
"name": "MyBlocklistIntegration",
"last_pull": "2024-09-17T07:06:21",
"event_type": "firewall_integration_offline"
}
}
JSON Schema
{
"$defs": {},
"type": "object",
"properties": {
"metadata": {
"type": "object",
"properties": {
"version": {
"type": "integer",
"const": 1
},
"issuer": {
"type": "string",
"const": "crowdsec.net"
}
},
"required": [
"version",
"issuer"
]
},
"details": {
"properties": {
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"id": {
"description": "ID of the blocklist integration",
"examples": [
"12345677732339c3d12345164a8426sbnk6ll4iaazda1234"
],
"title": "Id",
"type": "string"
},
"name": {
"description": "Name of the blocklist integration",
"examples": [
"MyBlocklistIntegration"
],
"title": "Name",
"type": "string"
},
"last_pull": {
"description": "Last time the blocklist integration pulled",
"examples": [
"2024-09-17T07:06:21"
],
"title": "Last Pull",
"type": "string"
},
"event_type": {
"const": "firewall_integration_offline",
"default": "firewall_integration_offline",
"title": "Event Type",
"type": "string"
}
},
"required": [
"event_id",
"organization_id",
"event_timestamp",
"id",
"name",
"last_pull",
"event_type"
],
"title": "FirewallIntegrationOffline",
"type": "object"
}
},
"required": [
"metadata",
"details"
]
}
Remediation Component Integration Offline
A Remediation Component Integration has been classified as offline.
This can happen for these scenarios:
- Remediation Component has not actively pulled the contents for over 24 hours.
{
"metadata": {
"version": 1,
"issuer": "crowdsec.net"
},
"details": {
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2021-07-29T12:00:00+00:00",
"id": "12345677732339c3d12345164a8426sbnk6ll4iaazda1234",
"name": "MyBlocklistIntegration",
"last_pull": "2024-09-17T07:06:21",
"event_type": "remediation_component_integration_offline"
}
}
JSON Schema
{
"$defs": {},
"type": "object",
"properties": {
"metadata": {
"type": "object",
"properties": {
"version": {
"type": "integer",
"const": 1
},
"issuer": {
"type": "string",
"const": "crowdsec.net"
}
},
"required": [
"version",
"issuer"
]
},
"details": {
"properties": {
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"id": {
"description": "ID of the blocklist integration",
"examples": [
"12345677732339c3d12345164a8426sbnk6ll4iaazda1234"
],
"title": "Id",
"type": "string"
},
"name": {
"description": "Name of the blocklist integration",
"examples": [
"MyBlocklistIntegration"
],
"title": "Name",
"type": "string"
},
"last_pull": {
"description": "Last time the blocklist integration pulled",
"examples": [
"2024-09-17T07:06:21"
],
"title": "Last Pull",
"type": "string"
},
"event_type": {
"const": "remediation_component_integration_offline",
"default": "remediation_component_integration_offline",
"title": "Event Type",
"type": "string"
}
},
"required": [
"event_id",
"organization_id",
"event_timestamp",
"id",
"name",
"last_pull",
"event_type"
],
"title": "RemediationComponentIntegrationOffline",
"type": "object"
}
},
"required": [
"metadata",
"details"
]
}
Log Processor No Alerts
A Log Processor has not pushed any alerts for over 48 hours.
{
"metadata": {
"version": 1,
"issuer": "crowdsec.net"
},
"details": {
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2021-07-29T12:00:00+00:00",
"id": "12345677732339c3d12345164a8426sbnk6ll4iaazda1234",
"name": "MyLogProcessor",
"version": "v1.6.3-rc4",
"event_type": "log_processor_no_alerts",
"last_push": "2025-05-17T07:06:21"
}
}
JSON Schema
{
"$defs": {},
"type": "object",
"properties": {
"metadata": {
"type": "object",
"properties": {
"version": {
"type": "integer",
"const": 1
},
"issuer": {
"type": "string",
"const": "crowdsec.net"
}
},
"required": [
"version",
"issuer"
]
},
"details": {
"properties": {
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"id": {
"description": "ID of the Log Processor",
"examples": [
"12345677732339c3d12345164a8426sbnk6ll4iaazda1234"
],
"title": "Id",
"type": "string"
},
"name": {
"description": "Name of the Log Processor",
"examples": [
"MyLogProcessor"
],
"title": "Name",
"type": "string"
},
"version": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "Version of the Log Processor",
"examples": [
"v1.6.3-rc4"
],
"title": "Version"
},
"last_push": {
"title": "Last Push",
"type": "string"
},
"event_type": {
"const": "log_processor_no_alerts",
"default": "log_processor_no_alerts",
"title": "Event Type",
"type": "string"
}
},
"required": [
"event_id",
"organization_id",
"event_timestamp",
"id",
"name",
"version",
"last_push",
"event_type"
],
"title": "LogProcessorNoAlerts",
"type": "object"
}
},
"required": [
"metadata",
"details"
]
}
CrowdSec Stack Component Outdated
A CrowdSec Stack Component is outdated.
This can happen for these scenarios:
- A new version of CrowdSec has been released.
- A new version of a Hub listed Remediation Component has been released**.
**The remediation component must send the semantic version to the Security Engine via the UserAgent header, note that all first party remediation components do this.
{
"metadata": {
"version": 1,
"issuer": "crowdsec.net"
},
"details": {
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2021-07-29T12:00:00+00:00",
"event_type": "component_outdated",
"nb_remediation_component": 10,
"nb_log_processor": 10,
"nb_security_engine": 10
}
}
JSON Schema
{
"$defs": {},
"type": "object",
"properties": {
"metadata": {
"type": "object",
"properties": {
"version": {
"type": "integer",
"const": 1
},
"issuer": {
"type": "string",
"const": "crowdsec.net"
}
},
"required": [
"version",
"issuer"
]
},
"details": {
"properties": {
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"event_type": {
"const": "component_outdated",
"default": "component_outdated",
"title": "Event Type",
"type": "string"
},
"nb_remediation_component": {
"description": "Number of remediation component",
"examples": [
10
],
"title": "Nb Remediation Component",
"type": "integer"
},
"nb_log_processor": {
"description": "Number of log processor",
"examples": [
10
],
"title": "Nb Log Processor",
"type": "integer"
},
"nb_security_engine": {
"description": "Number of security engine",
"examples": [
10
],
"title": "Nb Security Engine",
"type": "integer"
}
},
"required": [
"event_id",
"organization_id",
"event_timestamp",
"event_type",
"nb_remediation_component",
"nb_log_processor",
"nb_security_engine"
],
"title": "ComponentOutdated",
"type": "object"
}
},
"required": [
"metadata",
"details"
]
}
Log Processor Offline
A Log Processor has been offline for more than 24 hours.
{
"metadata": {
"version": 1,
"issuer": "crowdsec.net"
},
"details": {
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2021-07-29T12:00:00+00:00",
"id": "12345677732339c3d12345164a8426sbnk6ll4iaazda1234",
"name": "MyLogProcessor",
"version": "v1.6.3-rc4",
"last_update": "2024-09-17T07:06:21",
"event_type": "log_processor_offline"
}
}
JSON Schema
{
"$defs": {},
"type": "object",
"properties": {
"metadata": {
"type": "object",
"properties": {
"version": {
"type": "integer",
"const": 1
},
"issuer": {
"type": "string",
"const": "crowdsec.net"
}
},
"required": [
"version",
"issuer"
]
},
"details": {
"properties": {
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"id": {
"description": "ID of the Log Processor",
"examples": [
"12345677732339c3d12345164a8426sbnk6ll4iaazda1234"
],
"title": "Id",
"type": "string"
},
"name": {
"description": "Name of the Log Processor",
"examples": [
"MyLogProcessor"
],
"title": "Name",
"type": "string"
},
"version": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "Version of the Log Processor",
"examples": [
"v1.6.3-rc4"
],
"title": "Version"
},
"last_update": {
"description": "Last time the Log Processor updated",
"examples": [
"2024-09-17T07:06:21"
],
"title": "Last Update",
"type": "string"
},
"event_type": {
"const": "log_processor_offline",
"default": "log_processor_offline",
"title": "Event Type",
"type": "string"
}
},
"required": [
"event_id",
"organization_id",
"event_timestamp",
"id",
"name",
"version",
"last_update",
"event_type"
],
"title": "LogProcessorOffline",
"type": "object"
}
},
"required": [
"metadata",
"details"
]
}
Remediation Component Offline
A Remediation Component has not pulled from the Security Engine in over 24 hours.
{
"metadata": {
"version": 1,
"issuer": "crowdsec.net"
},
"details": {
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2021-07-29T12:00:00+00:00",
"id": "12345677732339c3d12345164a8426sbnk6ll4iaazda1234",
"name": "MyRemediationComponent",
"version": "v0.22",
"event_type": "remediation_component_offline",
"last_pull": "2024-09-17T07:06:21"
}
}
JSON Schema
{
"$defs": {},
"type": "object",
"properties": {
"metadata": {
"type": "object",
"properties": {
"version": {
"type": "integer",
"const": 1
},
"issuer": {
"type": "string",
"const": "crowdsec.net"
}
},
"required": [
"version",
"issuer"
]
},
"details": {
"properties": {
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"id": {
"description": "ID of the remediation component",
"examples": [
"12345677732339c3d12345164a8426sbnk6ll4iaazda1234"
],
"title": "Id",
"type": "string"
},
"name": {
"description": "Name of the remediation component",
"examples": [
"MyBlocklistIntegration"
],
"title": "Name",
"type": "string"
},
"version": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "Version of the remediation component",
"examples": [
"v0.22"
],
"title": "Version"
},
"last_pull": {
"title": "Last Pull",
"type": "string"
},
"event_type": {
"const": "remediation_component_offline",
"default": "remediation_component_offline",
"title": "Event Type",
"type": "string"
}
},
"required": [
"event_id",
"organization_id",
"event_timestamp",
"id",
"name",
"version",
"last_pull",
"event_type"
],
"title": "RemediationComponentOffline",
"type": "object"
}
},
"required": [
"metadata",
"details"
]
}
Security Engine No Alerts
A Security Engine has not pushed any alerts for over 48 hours.
{
"metadata": {
"version": 1,
"issuer": "crowdsec.net"
},
"details": {
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2021-07-29T12:00:00+00:00",
"id": "12345677732339c3d12345164a8426sbnk6ll4iaazda1234",
"version": "v1.6.3-rc4",
"os" : {"name" : "ubuntu", "version": "22.04"},
"last_push": "2024-09-17T07:06:21",
"event_type": "security_engine_no_alerts",
"name": "MySecurityEngine"
}
}
JSON Schema
{
"$defs": {
"OperatingSystem": {
"properties": {
"name": {
"title": "Name",
"type": "string"
},
"version": {
"title": "Version",
"type": "string"
}
},
"required": [
"name",
"version"
],
"title": "OperatingSystem",
"type": "object"
}
},
"type": "object",
"properties": {
"metadata": {
"type": "object",
"properties": {
"version": {
"type": "integer",
"const": 1
},
"issuer": {
"type": "string",
"const": "crowdsec.net"
}
},
"required": [
"version",
"issuer"
]
},
"details": {
"properties": {
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"id": {
"description": "ID of the security engine",
"examples": [
"12345677732339c3d12345164a8426sbnk6ll4iaazda1234"
],
"title": "Id",
"type": "string"
},
"version": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "Version of the security engine",
"examples": [
"v1.6.3-rc4"
],
"title": "Version"
},
"os": {
"anyOf": [
{
"$ref": "#/$defs/OperatingSystem"
},
{
"type": "null"
}
],
"default": null,
"description": "Operating System of the security engine",
"examples": [
"Linux"
]
},
"last_push": {
"description": "Last time the security engine pushed",
"examples": [
"2024-09-17T07:06:21"
],
"title": "Last Push",
"type": "string"
},
"event_type": {
"const": "security_engine_no_alerts",
"default": "security_engine_no_alerts",
"title": "Event Type",
"type": "string"
},
"name": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"description": "Name of the security engine",
"examples": [
"MySecurityEngine"
],
"title": "Name"
}
},
"required": [
"event_id",
"organization_id",
"event_timestamp",
"id",
"version",
"os",
"last_push",
"event_type",
"name"
],
"title": "SecurityEngineNoAlerts",
"type": "object"
}
},
"required": [
"metadata",
"details"
]
}
Security Engine Offline
A Security Engine has been offline for more than 48 hours.
{
"metadata": {
"version": 1,
"issuer": "crowdsec.net"
},
"details": {
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2021-07-29T12:00:00+00:00",
"id": "12345677732339c3d12345164a8426sbnk6ll4iaazda1234",
"version": "v1.6.3-rc4",
"os" : {"name" : "ubuntu", "version": "22.04"},
"event_type": "security_engine_offline",
"last_login": "2024-09-17T07:06:21",
"name": "MySecurityEngine"
}
}
JSON Schema
{
"$defs": {
"OperatingSystem": {
"properties": {
"name": {
"title": "Name",
"type": "string"
},
"version": {
"title": "Version",
"type": "string"
}
},
"required": [
"name",
"version"
],
"title": "OperatingSystem",
"type": "object"
}
},
"type": "object",
"properties": {
"metadata": {
"type": "object",
"properties": {
"version": {
"type": "integer",
"const": 1
},
"issuer": {
"type": "string",
"const": "crowdsec.net"
}
},
"required": [
"version",
"issuer"
]
},
"details": {
"properties": {
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"id": {
"description": "ID of the security engine",
"examples": [
"12345677732339c3d12345164a8426sbnk6ll4iaazda1234"
],
"title": "Id",
"type": "string"
},
"version": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "Version of the security engine",
"examples": [
"v1.6.3-rc4"
],
"title": "Version"
},
"os": {
"anyOf": [
{
"$ref": "#/$defs/OperatingSystem"
},
{
"type": "null"
}
],
"default": null,
"description": "Operating System of the security engine",
"examples": [
"Linux"
]
},
"last_login": {
"title": "Last Login",
"type": "string"
},
"event_type": {
"const": "security_engine_offline",
"default": "security_engine_offline",
"title": "Event Type",
"type": "string"
},
"name": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"description": "Name of the security engine",
"examples": [
"MySecurityEngine"
],
"title": "Name"
}
},
"required": [
"event_id",
"organization_id",
"event_timestamp",
"id",
"version",
"os",
"last_login",
"event_type",
"name"
],
"title": "SecurityEngineOffline",
"type": "object"
}
},
"required": [
"metadata",
"details"
]
}
Blocking Known Safe IP
A known safe or legitimate IP address was blocked (false positive)
{
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2025-07-10T09:11:33.359703Z",
"event_type": "blocking_safe_ip",
"uuid": "alert-uuid-1234",
"message": "Suspicious SSH behavior detected",
"scenario": "ssh-brute-force",
"behaviors": [
{
"name": "Brute Force",
"description": "Multiple failed SSH login attempts detected in short time",
"label": "SSH Brute Force"
},
{
"name": "Port Scan",
"description": "Scanning activity detected on multiple ports",
"label": "Scan"
}
],
"start_at": "2025-07-10T09:11:26.584612Z",
"stop_at": "2025-07-10T09:11:26.584612Z",
"target": {
"ip": "192.168.1.10",
"id": "machine-01",
"name": "internal-server-01"
},
"source": {
"scope": "ip",
"value": "203.0.113.25",
"as_name": "ExampleISP",
"as_number": 64512,
"country": "US",
"city": "San Francisco",
"latitude": 37.7749,
"longitude": -122.4194,
"rdns": "25.113.0.203.example.com"
},
"is_manual_decision": false,
"scenario_confidence": 0,
"false_positives": [
{
"name": "cdn:example_exit_node",
"description": "IP is an Example CDN exit IP and should not be flagged as a threat.",
"label": "Example CDN"
}
]
}
JSON Schema
{
"$defs": {
"AlertBehavior": {
"properties": {
"description": {
"description": "The attack behavior description",
"title": "Description",
"type": "string"
},
"label": {
"description": "The attack behavior label",
"title": "Label",
"type": "string"
},
"name": {
"description": "The attack behavior name",
"title": "Name",
"type": "string"
}
},
"required": [
"name",
"description",
"label"
],
"title": "AlertBehavior",
"type": "object"
},
"AlertSource": {
"properties": {
"as_name": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "The AS name of the source",
"title": "As Name"
},
"as_number": {
"anyOf": [
{
"type": "integer"
},
{
"type": "null"
}
],
"default": null,
"description": "The AS number of the source",
"title": "As Number"
},
"city": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "The city of the source",
"title": "City"
},
"country": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "The country of the source",
"title": "Country"
},
"latitude": {
"anyOf": [
{
"type": "number"
},
{
"type": "null"
}
],
"default": null,
"description": "The latitude of the source",
"title": "Latitude"
},
"longitude": {
"anyOf": [
{
"type": "number"
},
{
"type": "null"
}
],
"default": null,
"description": "The longitude of the source",
"title": "Longitude"
},
"rdns": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "The rDNS of the source",
"title": "Rdns"
},
"scope": {
"description": "The scope of the value",
"title": "Scope",
"type": "string"
},
"value": {
"description": "The value of the source",
"title": "Value",
"type": "string"
}
},
"required": [
"scope",
"value"
],
"title": "AlertSource",
"type": "object"
},
"AlertTarget": {
"properties": {
"id": {
"description": "The id of the machine targeted by the attack",
"title": "Id",
"type": "string"
},
"ip": {
"description": "The IP targeted by the attack",
"title": "Ip",
"type": "string"
},
"name": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "The name of the machine targeted by the attack",
"title": "Name"
}
},
"required": [
"ip",
"id"
],
"title": "AlertTarget",
"type": "object"
},
"FalsePositive": {
"properties": {
"description": {
"description": "The description of the false positive",
"title": "Description",
"type": "string"
},
"label": {
"description": "The label of the false positive",
"title": "Label",
"type": "string"
},
"name": {
"description": "The name of the false positive",
"title": "Name",
"type": "string"
}
},
"required": [
"name",
"description",
"label"
],
"title": "FalsePositive",
"type": "object"
}
},
"properties": {
"behaviors": {
"default": [],
"description": "The attack behaviors",
"items": {
"$ref": "#/$defs/AlertBehavior"
},
"title": "Behaviors",
"type": "array"
},
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"event_type": {
"const": "blocking_safe_ip",
"default": "blocking_safe_ip",
"title": "Event Type",
"type": "string"
},
"false_positives": {
"anyOf": [
{
"items": {
"$ref": "#/$defs/FalsePositive"
},
"type": "array"
},
{
"type": "null"
}
],
"description": "List of false positive identifiers",
"title": "False Positives"
},
"is_manual_decision": {
"default": false,
"description": "Whether the decision was created manually",
"title": "Is Manual Decision",
"type": "boolean"
},
"message": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "The alert message",
"title": "Message"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"scenario": {
"description": "The attack scenario",
"title": "Scenario",
"type": "string"
},
"scenario_confidence": {
"default": 0,
"description": "The confidence of the scenario",
"title": "Scenario Confidence",
"type": "integer"
},
"source": {
"$ref": "#/$defs/AlertSource",
"description": "The source of the attack"
},
"start_at": {
"description": "The attack start time",
"format": "date-time",
"title": "Start At",
"type": "string"
},
"stop_at": {
"description": "The attack stop time",
"format": "date-time",
"title": "Stop At",
"type": "string"
},
"target": {
"$ref": "#/$defs/AlertTarget",
"description": "The target of the attack"
},
"uuid": {
"anyOf": [
{
"type": "string"
},
{
"type": "null"
}
],
"default": null,
"description": "The alert UUID",
"title": "Uuid"
}
},
"required": [
"organization_id",
"scenario",
"start_at",
"stop_at",
"target",
"source",
"false_positives"
],
"title": "BlockingSafeIP",
"type": "object"
}
Admin
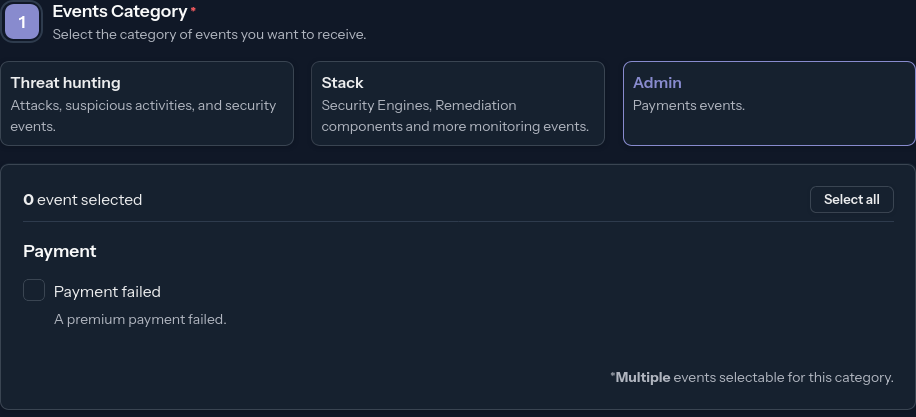
Payment Failed
A payment attempt for your enterprise subscription failed.
This can happen for these scenarios:
- Payment needs additional approval from your bank.
- You have insufficient funds to complete the transaction.
{
"metadata": {
"version": 1,
"issuer": "crowdsec.net"
},
"details": {
"event_id": "c6d468d4f1084ebca84165c33f97fbc4",
"organization_id": "12345678-1234-1234-1234-123456789012",
"event_timestamp": "2021-07-29T12:00:00+00:00",
"event_type": "payment_failed"
}
}
JSON Schema
{
"$defs": {},
"type": "object",
"properties": {
"metadata": {
"type": "object",
"properties": {
"version": {
"type": "integer",
"const": 1
},
"issuer": {
"type": "string",
"const": "crowdsec.net"
}
},
"required": [
"version",
"issuer"
]
},
"details": {
"properties": {
"event_id": {
"description": "ID of the source event",
"examples": [
"c6d468d4f1084ebca84165c33f97fbc4"
],
"title": "Event Id",
"type": "string"
},
"organization_id": {
"description": "Organization ID of the source event",
"examples": [
"12345678-1234-1234-1234-123456789012"
],
"title": "Organization Id",
"type": "string"
},
"event_timestamp": {
"description": "Timestamp of the source event",
"examples": [
"2021-07-29T12:00:00+00:00"
],
"format": "date-time",
"title": "Event Timestamp",
"type": "string"
},
"event_type": {
"const": "payment_failed",
"default": "payment_failed",
"title": "Event Type",
"type": "string"
}
},
"required": [
"event_id",
"organization_id",
"event_timestamp",
"event_type"
],
"title": "PremiumPaymentFailed",
"type": "object"
}
},
"required": [
"metadata",
"details"
]
}
Troubleshooting
Network error
If you are unable to ping your webhook URL, this may be because of networking problem.
The webhook integration is allowed to send HTTP request on the following port:
8080804438443

